Tuesday, September 22, 2015
CEH Certified Ethical Hacker Version 8 Study Guide (e-book)
Prepare for the new Certified Ethical Hacker version 8 exam with this Sybex guide
Security professionals remain in high demand. The Certified Ethical Hacker is a one-of-a-kind certification designed to give the candidate a look inside the mind of a hacker. This study guide provides a concise, easy-to-follow approach that covers all of the exam objectives and includes numerous examples and hands-on exercises. Coverage includes cryptography, footprinting and reconnaissance, scanning networks, enumeration of services, gaining access to a system, Trojans, viruses, worms, covert channels, and much more. A companion website includes additional study tools, Including practice exam and chapter review questions and electronic flashcards. * Security remains the fastest growing segment of IT, and CEH certification provides unique skills * The CEH also satisfies the Department of Defense's 8570 Directive, which requires all Information Assurance government positions to hold one of the approved certifications * This Sybex study guide is perfect for candidates studying on their own as well as those who are taking the CEHv8 course * Covers all the exam objectives with an easy-to-follow approach * Companion website includes practice exam questions, flashcards, and a searchable Glossary of key terms
CEH Certified Ethical Hacker Study Guide V413HAV (e-book)
Full Coverage of All Exam Objectives for the CEH Exams 312-50 and EC0-350 Thoroughly prepare for the challenging CEH Certified Ethical Hackers exam with this comprehensive study guide. The book provides full coverage of exam topics, real-world examples, and includes a CD with chapter review questions, two full-length practice exams, electronic flashcards, a glossary of key terms, and the entire book in a searchable pdf e-book. What's Inside: Covers ethics and legal issues, footprinting, scanning, enumeration, system hacking, trojans and backdoors, sniffers, denial of service, social engineering, session hijacking, hacking Web servers, Web application vulnerabilities,
CEH Certified Ethical Hacker More Than 100 Success Secrets (e-book)
The Certified Ethical Hacker (CEH) is a professional certification provided by the International Council of E-Commerce Consultants (EC-Council.) An Ethical Hacker is one name given to a Penetration Tester. An ethical hacker is usually employed by an organization who trusts him to attempt to penetrate networks and/or computer systems, using the same methods as a hacker, for the purpose of finding and fixing computer security vulnerabilities. This book is a perfect review for people who are knowledgeable on the subject of ethical hacking, desire certification, and want that last minute review and prep guide before going in for the exam. It is cost effective and to the point! Many guides already exist to teach the subject of ethical hacking.
A Hacker's Life Starter - Benjamin James (e-book)
How many people have you seen with the fantasy of learning hacking? A lot right? Now how many books you read with the material of hacking that didn't enlight you step-by-step?A few right? The A hacker's Life Starter will be demonstrating the most demanding topics used everyday in the society hacking world. In has everything a beginner or a professional would like to exercise and play with everyday. Because every single exercise are structured step-by-step. You will learn things like: The Hackers Tool Making Virus Cracking File Passwords Backtrack/Kali Hack Smart Phones Break .rar file SQL injection Phishing Denial of Service Wireless Hack Securing yourself And much more..
Wednesday, March 18, 2015
FL Studio Producer Edition 11.1.1 (32-64 bit) (Reg R2R)
Introducing FL Studio 11
FL Studio 11 is a complete software music production environment, representing more than 14 years of innovative developments and our commitment to Lifetime Free Updates. Everything you need in one package to compose, arrange, record, edit, mix and master professional quality music.
FL Studio 11 is the fastest way from your brain to your speakers.
What can FL Studio 11 do?
* Audio editing and manipulation including pitch correction, pitch shifting, harmonization, time-stretching, beat-detection & slicing, audio warping and standard audio manipulation (cut/paste etc).
* Automate most interface and all plugin parameters by recording, drawing, spline-based automation curves, automation generators with formula based control of links.
* Be hosted in other DAWs as a VST or connected through ReWire.
* Live music performance including video effect visualization.
* Mix and remix audio including apply real-time audio effects including delay, reverb & filtering.
* Multi-track audio recording up to the limit of your audio-interface inputs.
* Record & play MIDI input recording from keyboards, drum pads and controllers.
* Sequencing and arranging with pattern and linear workflow possible.
* Synthesizer & effect plugin hosting VST 32 & 64 bit, DX and FL Native formats.
Street Hacker
onsole-based games like Street Hacker introduce a new form of heart-pumping adrenaline which cannot be reproduced outside of this gaming genre. Use brute-force generators, port scanners, and IP scanners and exploit scripts, viruses, worms, and Trojans to help you hack the streets in 8 of Americans biggest cities. Become a part of this extremely dynamic simulator and choose your own allies in the hacker's war for the world.
Uplink Hacker Elite
If he were still allowed to own a computer, Kevin Mitnick would undoubtedly approve of Uplink. Available only by direct order from the UK-based developer, Introversion Software's new strategy game seems to have been made for the infamous super hacker, given that the sole objective of play is to break into as many computer systems as possible. Success is measured in terms of altered, stolen, and destroyed data, and of course in being able to get in and out before tracer software gives your address to those friendly people at the FBI.
Monday, March 16, 2015
Resource Hacker 3.6.0.92
Resource Hacker is a freeware utility to view, modify, rename, add, delete and extract resources in 32bit Windows executables and resource files (RES). It incorporates an internal resource script compiler and decompiler and works on Win95, Win98, WinME, WinNT, Win2000 and WinXP operating systems.
Viewing Resources: Cursor, Icon, Bitmap, GIF, AVI, and JPG resource images can be viewed. WAV and MIDI audio resources can be played. Menus, Dialogs, MessageTables, StringTables, Accelerators, Delphi Forms, and VersionInfo resources can be viewed as decompiled resource scripts. Menus and Dialogs can also be viewed as they would appear in a running application.
Adobe Illustrator CC 17.0.0 Final Multilanguage x86 + x64+ Crack
Adobe Illustrator is a vector graphics editor developed and marketed by Adobe Systems. The latest version is Illustrator CC..
NEW Touch Type tool - Design with type in a powerful new way. Characters can now be manipulated like individual objects. Experiment with moving, scaling, and rotating, knowing you can change the font or edit at any time. And you can now use multitouch devices as well as a mouse or stylus.
NEW Images in brushes - Paint with a brush made from a photo. Art, Pattern, and Scatter brushes can contain raster images, so you can create complex organic designs quickly with simple brush strokes. As with all Illustrator brushes, your strokes can be reshaped and modified at will.
NEW Font search - Find the perfect font fast. In the Character panel, type a style such as “bold” or “italic,” a font family, or any other part of a font name. You’ll get a filtered view that lets you see just the fonts that match your criteria.
PowerISO v4.5 Retail
Supported operating systems:
32-bit Windows: Windows 98, Windows Me, Windows 2000, Windows XP, Windows 2003, Windows Vista, Windows 2008, Windows 7, Windows 8 / 8.1
64-bit Windows: Windows XP, Windows 2003, Windows Vista, Windows 2008, Windows 7, Windows 8 / 8.1
Friday, March 6, 2015
Oracle 11g Anti-Hacker's Cookbook (e-book)
Make your Oracle database virtually impregnable to hackers using the knowledge in this book. With over 50 recipes, you’ll quickly learn protection methodologies that use industry certified techniques to secure the Oracle database server.
Learn to protect your sensitive data by using industry certified techniques
Implement and use ultimate techniques in Oracle Security and new security features introduced in Oracle 11g R2
Implement strong network communication security using different encryption solutions provided by Oracle Advanced Security
In Detail
For almost all organizations, data security is a matter of prestige and credibility. The Oracle Database is one of the most rich in features and probably the most used Database in a variety of industries where security is essential. To ensure security of data both in transit and on the disk, Oracle has implemented the security technologies to achieve a reliable and solid system. In Oracle 11g Anti-Hacker's Cookbook, you will learn about the most important solutions that can be used for better database security
"Oracle 11g Anti-hacker's Cookbook" covers all the important security measures and includes various tips and tricks to protect your Oracle Database.
"Oracle 11g Anti-hacker's Cookbook" uses real-world scenarios to show you how to secure the Oracle Database server from different perspectives and against different attack scenarios. Almost every chapter has a possible threads section, which describes the major dangers that can be confronted. The initial chapters cover how to defend the operating system, the network, the data and the users. The defense scenarios are linked and designed to prevent these attacks. The later chapters cover Oracle Vault, Oracle VPD, Oracle Labels, and Oracle Audit. Finally, in the Appendices, the book demonstrates how to perform a security assessment against the operating system and the database, and how to use a DAM tool for monitoring.
What you will learn from this book
Get to grips with configuring a secure server at operating system level for Oracle Database
Master how to secure data by using Oracle Cryptographic API and Transparent Data Encryption
Get step-by-step instructions to implement a solid audit strategy by using the built in solutions and fine grained auditing
Understand how to segregate and protect data access by using Oracle Vault
Learn about different types of attacks and how to implement a solid defence against them
Empathize the attacks and interceptions by using different techniques and tools such as sniffing, man-in-the-middle, brute force and password crackers.
Approach
This cookbook has recipes written in simple, easy to understand format with lots of screenshots and insightful tips and hints.
Who this book is written for
If you are an Oracle Database Administrator, Security Manager or Security Auditor looking to secure the Oracle Database or prevent it from being hacked, then this book is for you
This book assumes you have a basic understanding of security concepts.
Download : Oracle 11g Anti-Hacker's Cookbook (e-book)
Network Forensics: Tracking Hackers through Cyberspace (e-book)
“This is a must-have work for anybody in information security, digital forensics, or involved with incident handling. As we move away from traditional disk-based analysis into the interconnectivity of the cloud, Sherri and Jonathan have created a framework and roadmap that will act as a seminal work in this developing field.”
– Dr. Craig S. Wright (GSE), Asia Pacific Director at Global Institute for Cyber Security + Research.
“It’s like a symphony meeting an encyclopedia meeting a spy novel.”
–Michael Ford, Corero Network Security
On the Internet, every action leaves a mark–in routers, firewalls, web proxies, and within network traffic itself. When a hacker breaks into a bank, or an insider smuggles secrets to a competitor, evidence of the crime is always left behind.
Learn to recognize hackers’ tracks and uncover network-based evidence in Network Forensics: Tracking Hackers through Cyberspace. Carve suspicious email attachments from packet captures. Use flow records to track an intruder as he pivots through the network. Analyze a real-world wireless encryption-cracking attack (and then crack the key yourself). Reconstruct a suspect’s web surfing history–and cached web pages, too–from a web proxy. Uncover DNS-tunneled traffic. Dissect the Operation Aurora exploit, caught on the wire.
Throughout the text, step-by-step case studies guide you through the analysis of network-based evidence. You can download the evidence files from the authors’ web site (lmgsecurity.com), and follow along to gain hands-on experience.
Hackers leave footprints all across the Internet. Can you find their tracks and solve the case? Pick up Network Forensics and find out.
Download : Network Forensics: Tracking Hackers through Cyberspace (e-book)
Maximum Security - A Hacker's Guide to Protecting Your Inter (e-book)
Now more than ever, it is imperative that users be able to protect their system from hackers trashing their Web sites or stealing information. Written by a reformed hacker, this comprehensive resource identifies security holes in common computer and network systems, allowing system administrators to discover faults inherent within their network- and work toward a solution to those problems.
Download : Maximum Security - A Hacker's Guide to Protecting Your Inter.pdf
Friday, February 27, 2015
Debian 7.6.0 AMD64 Gnome Desktop
Debian remains one of the most important projects in Linux. Debian 7 offers some significant improvements, and it certainly warrants an upgrade if you are using an older version of Debian.
No doubt that some folks will be disappointed by the lack of support for Secure Boot, but I don’t think that that should be a deal breaker. The support for UEFI in 64-bit PCs is a step forward that will be built on later, so I try to take the long view on this issue.
Some will take issue with my comments about the forced inclusion of the ad blocker in Iceweasel, but I think it’s something worth talking about since Debian 7 is such an important Linux project. I fully understand that some folks hate ads and will block them, that is their right. However, advertising remains the basis for free content like this review, so it’s worth noting and thinking about the ramifications of browsers having ad blockers installed by default.
Debian 7 is best suited to intermediate and advanced Linux users. However, I urge beginners to learn more about it. Don’t be afraid at giving it a try in a virtual machine or as a live distro. Understanding Debian can teach you a lot about Linux, and you’ll have the opportunity to learn why it is the foundation for so many other distros.
Download : debian-live-7.6.0-amd64-gnome-desktop.iso
Debian 6.x.x
Debian 6.0 includes the KDE Plasma Desktop and Applications, the GNOME, Xfce, and LXDE desktop environments as well as all kinds of server applications. It also features compatibility with the FHS v2.3 and software developed for version 3.2 of the LSB.
Debian runs on computers ranging from palmtops and handheld systems to supercomputers, and on nearly everything in between. A total of nine architectures are supported by Debian GNU/Linux: 32-bit PC / Intel IA-32 (i386), 64-bit PC / Intel EM64T / x86-64 (amd64), Motorola/IBM PowerPC (powerpc), Sun/Oracle SPARC (sparc), MIPS (mips (big-endian) and mipsel (little-endian)), Intel Itanium (ia64), IBM S/390 (s390), and ARM EABI (armel).
Debian 6.0 Squeeze introduces technical previews of two new ports to the kernel of the FreeBSD project using the known Debian/GNU userland: Debian GNU/kFreeBSD for the 32-bit PC (kfreebsd-i386) and the 64-bit PC (kfreebsd-amd64). These ports are the first ones ever to be included in a Debian release which are not based on the Linux kernel. The support of common server software is strong and combines the existing features of Linux-based Debian versions with the unique features known from the BSD world. However, for this release these new ports are limited; for example, some advanced desktop features are not yet supported.
Another first is the completely free Linux kernel, which no longer contains problematic firmware files. These were split out into separate packages and moved out of the Debian main archive into the non-free area of our archive, which is not enabled by default. In this way Debian users have the possibility of running a completely free operating system, but may still choose to use non-free firmware files if necessary. Firmware files needed during installation may be loaded by the installation system; special CD images and tarballs for USB based installations are available too. More information about this may be found in the Debian Firmware wiki page.
Furthermore, Debian 6.0 introduces a dependency based boot system, making system start-up faster and more robust due to parallel execution of boot scripts and correct dependency tracking between them. Various other changes make Debian more suitable for small form factor notebooks, like the introduction of the KDE Plasma Netbook shell.
This release includes numerous updated software packages, such as:
- KDE Plasma Workspaces and KDE Applications 4.4.5
- an updated version of the GNOME desktop environment 2.30
- the Xfce 4.6 desktop environment
- LXDE 0.5.0
- X.Org 7.5
- OpenOffice.org 3.2.1
- GIMP 2.6.11
- Iceweasel 3.5.16 (an unbranded version of Mozilla Firefox)
- Icedove 3.0.11 (an unbranded version of Mozilla Thunderbird)
- PostgreSQL 8.4.6
- MySQL 5.1.49
- GNU Compiler Collection 4.4.5
- Linux 2.6.32
- Apache 2.2.16
- Samba 3.5.6
- Python 2.6.6, 2.5.5 and 3.1.3
- Perl 5.10.1
- PHP 5.3.3
- Asterisk 1.6.2.9
- Nagios 3.2.3
- Xen Hypervisor 4.0.1 (dom0 as well as domU support)
- OpenJDK 6b18
- Tomcat 6.0.18
more than 29,000 other ready-to-use software packages, built from nearly 15,000 source packages.
Debian 6.0 includes over 10,000 new packages like the browser Chromium, the monitoring solution Icinga, the package management frontend Software Center, the network manager wicd, the Linux container tools lxc and the cluster framework Corosync.
With this broad selection of packages, Debian once again stays true to its goal of being the universal operating system. It is suitable for many different use cases: from desktop systems to netbooks; from development servers to cluster systems; and for database, web or storage servers. At the same time, additional quality assurance efforts like automatic installation and upgrade tests for all packages in Debian's archive ensure that Debian 6.0 fulfils the high expectations that users have of a stable Debian release. It is rock solid and rigorously tested.
Starting from Debian 6.0, the Custom Debian Distributions are renamed to Debian Pure Blends. Their coverage has increased as Debian 6.0 adds Debian Accessibility, DebiChem, Debian EzGo, Debian GIS and Debian Multimedia to the already existing Debian Edu, Debian Med and Debian Science pure blends. The full content of all the blends can be browsed, including prospective packages that users are welcome to nominate for addition to the next release.
Debian may be installed from various installation media such as Blu-ray Discs, DVDs, CDs and USB sticks or from the network. GNOME is the default desktop environment and is contained on the first CD. Other desktop environments — KDE Plasma Desktop and Applications, Xfce, or LXDE — may be installed through two alternative CD images. The desired desktop environment may also be chosen from the boot menus of the CDs/DVDs. Again available with Debian 6.0 are multi-architecture CDs and DVDs which support installation of multiple architectures from a single disc. The creation of bootable USB installation media has also been greatly simplified; see the Installation Guide for more details.
In addition to the regular installation media, Debian GNU/Linux may also be directly used without prior installation. The special images used, known as live images, are available for CDs, USB sticks and netboot setups. Initially, these are provided for the amd64 and i386 architectures only. It is also possible to use these live images to install Debian GNU/Linux.
The installation process for Debian GNU/Linux 6.0 has been improved in various ways, including easier selection of language and keyboard settings, and partitioning of logical volumes, RAID and encrypted systems. Support has also been added for the ext4 and Btrfs filesystems and — on the kFreeBSD architecture — the Zettabyte filesystem (ZFS). The installation system for Debian GNU/Linux is now available in 70 languages.
Debian installation images may be downloaded right now via BitTorrent (the recommended method), jigdo or HTTP; see Debian on CDs for further information. It will soon be available on physical DVD, CD-ROM and Blu-ray Discs from numerous vendors, too.
Upgrades to Debian GNU/Linux 6.0 from the previous release, Debian GNU/Linux 5.0 (codenamed Lenny), are automatically handled by the apt-get package management tool for most configurations, and to a certain degree also by the aptitude package management tool. As always, Debian GNU/Linux systems may be upgraded painlessly, in place, without any forced downtime, but it is strongly recommended to read the release notes as well as the installation guide for possible issues, and for detailed instructions on installing and upgrading. The release notes will be further improved and translated to additional languages in the weeks after the release.
About Debian
Debian is a free operating system, developed by thousands of volunteers from all over the world who collaborate via the Internet. The Debian project's key strengths are its volunteer base, its dedication to the Debian Social Contract and Free Software, and its commitment to provide the best operating system possible. Debian 6.0 is another important step in that direction.
Download : debian-6.0.0-i386-CD-1.iso
- the Xfce 4.6 desktop environment
- LXDE 0.5.0
- X.Org 7.5
- OpenOffice.org 3.2.1
- GIMP 2.6.11
- Iceweasel 3.5.16 (an unbranded version of Mozilla Firefox)
- Icedove 3.0.11 (an unbranded version of Mozilla Thunderbird)
- PostgreSQL 8.4.6
- MySQL 5.1.49
- GNU Compiler Collection 4.4.5
- Linux 2.6.32
- Apache 2.2.16
- Samba 3.5.6
- Python 2.6.6, 2.5.5 and 3.1.3
- Perl 5.10.1
- PHP 5.3.3
- Asterisk 1.6.2.9
- Nagios 3.2.3
- Xen Hypervisor 4.0.1 (dom0 as well as domU support)
- OpenJDK 6b18
- Tomcat 6.0.18
more than 29,000 other ready-to-use software packages, built from nearly 15,000 source packages.
Debian 6.0 includes over 10,000 new packages like the browser Chromium, the monitoring solution Icinga, the package management frontend Software Center, the network manager wicd, the Linux container tools lxc and the cluster framework Corosync.
With this broad selection of packages, Debian once again stays true to its goal of being the universal operating system. It is suitable for many different use cases: from desktop systems to netbooks; from development servers to cluster systems; and for database, web or storage servers. At the same time, additional quality assurance efforts like automatic installation and upgrade tests for all packages in Debian's archive ensure that Debian 6.0 fulfils the high expectations that users have of a stable Debian release. It is rock solid and rigorously tested.
Starting from Debian 6.0, the Custom Debian Distributions are renamed to Debian Pure Blends. Their coverage has increased as Debian 6.0 adds Debian Accessibility, DebiChem, Debian EzGo, Debian GIS and Debian Multimedia to the already existing Debian Edu, Debian Med and Debian Science pure blends. The full content of all the blends can be browsed, including prospective packages that users are welcome to nominate for addition to the next release.
Debian may be installed from various installation media such as Blu-ray Discs, DVDs, CDs and USB sticks or from the network. GNOME is the default desktop environment and is contained on the first CD. Other desktop environments — KDE Plasma Desktop and Applications, Xfce, or LXDE — may be installed through two alternative CD images. The desired desktop environment may also be chosen from the boot menus of the CDs/DVDs. Again available with Debian 6.0 are multi-architecture CDs and DVDs which support installation of multiple architectures from a single disc. The creation of bootable USB installation media has also been greatly simplified; see the Installation Guide for more details.
In addition to the regular installation media, Debian GNU/Linux may also be directly used without prior installation. The special images used, known as live images, are available for CDs, USB sticks and netboot setups. Initially, these are provided for the amd64 and i386 architectures only. It is also possible to use these live images to install Debian GNU/Linux.
The installation process for Debian GNU/Linux 6.0 has been improved in various ways, including easier selection of language and keyboard settings, and partitioning of logical volumes, RAID and encrypted systems. Support has also been added for the ext4 and Btrfs filesystems and — on the kFreeBSD architecture — the Zettabyte filesystem (ZFS). The installation system for Debian GNU/Linux is now available in 70 languages.
Debian installation images may be downloaded right now via BitTorrent (the recommended method), jigdo or HTTP; see Debian on CDs for further information. It will soon be available on physical DVD, CD-ROM and Blu-ray Discs from numerous vendors, too.
Upgrades to Debian GNU/Linux 6.0 from the previous release, Debian GNU/Linux 5.0 (codenamed Lenny), are automatically handled by the apt-get package management tool for most configurations, and to a certain degree also by the aptitude package management tool. As always, Debian GNU/Linux systems may be upgraded painlessly, in place, without any forced downtime, but it is strongly recommended to read the release notes as well as the installation guide for possible issues, and for detailed instructions on installing and upgrading. The release notes will be further improved and translated to additional languages in the weeks after the release.
About Debian
Debian is a free operating system, developed by thousands of volunteers from all over the world who collaborate via the Internet. The Debian project's key strengths are its volunteer base, its dedication to the Debian Social Contract and Free Software, and its commitment to provide the best operating system possible. Debian 6.0 is another important step in that direction.
Download : debian-6.0.0-i386-CD-1.iso
Downlaod : debian-6.0.5-i386-DVD-1.iso
Download : debian-6.0.5-i386-netinst.iso
Sunday, February 22, 2015
Windows 7 Sp1 Ultimate en-US (x86)
If you want to run Windows 7 on your PC, here's what it takes:
- 1 gigahertz (GHz) or faster 32-bit (x86) or 64-bit (x64) processor
- 1 gigabyte (GB) RAM (32-bit) or 2 GB RAM (64-bit)
- 16 GB available hard disk space (32-bit) or 20 GB (64-bit)
- DirectX 9 graphics device with WDDM 1.0 or higher driver
Additional requirements to use certain features:
- Internet access (fees may apply)
- Depending on resolution, video playback may require additional memory and advanced graphics hardware
- Some games and programs might require a graphics card compatible with DirectX 10 or higher for optimal performance
- For some Windows Media Center functionality a TV tuner and additional hardware may be required
- Windows Touch and Tablet PCs require specific hardware
- HomeGroup requires a network and PCs running Windows 7
- DVD/CD authoring requires a compatible optical drive
- BitLocker requires Trusted Platform Module (TPM) 1.2
- BitLocker To Go requires a USB flash drive
- Windows XP Mode requires an additional 1 GB of RAM and an additional 15 GB of available hard disk space.
- Music and sound require audio output
PCs with multi-core processors:
Windows 7 was designed to work with today's multi-core processors. All 32-bit versions of Windows 7 can support up to 32 processor cores, while 64‑bit versions can support up to 256 processor cores.
PCs with multiple processors (CPUs):
Commercial servers, workstations, and other high-end PCs may have more than one physical processor. Windows 7 Professional, Enterprise, and Ultimate allow for two physical processors, providing the best performance on these computers. Windows 7 Starter, Home Basic, and Home Premium will recognize only one physical processor.
Downlaod Windows 7 Sp1 Ultimate en-US (x86) (AlbDll.com) 3 G
Password for Zip Archive is : AlbDll.com
Windows 8.1 Preactived V2 Office 2013 Pro Plus
No Windows 8.1 Settings were harmed in the making of this ISO
No Programs are added to Windows
No Registry Settings were modified
No Unattended Settings were added to the ISO
Installation Indexes:
Windows 8.1 (Core) x64 / KMS-Activated
Windows 8.1 (Core) N x64 / KMS-Activated
Windows 8.1 (Core) Single Language x64 / KMS-Activated
Windows 8.1 Pro x64 / KMS-Activated
Tools used:
imagex for /flags "ProfessionalWMC" setting and index renames
dism for set-edition for ProWMC, KB integration, install.esd export
oscdimg for ISO mastering with MS's default -u1 option
Info folder added to Windows Setup folder to annoy credit theives
Features:
Non-Activated and Pre-Activated indexes. Take your pick.*
*Uses custom AutoKMS_VL_ALL folder in Windows directory. You can
uninstall the daily task there if you wish to use a different
activator later. I've included the uninstall script
Highly Compressed install.esd recovery compression format
UEFI boot information added to ISO boot data
Notes
v1 was missing the non-activated ProWMC index. Nothing else was wrong
with it. You don't need to download this if you don't want the ProWMC
index. Nothing is different except the additional index and a slightly
newer version of the activator. If you have v1, this activator will
likely not fix any issues you have with it
First proper Win81AIO with pre-activation
All indexes use original MSDN 9/9 Win8.1 isos with integrated hotfixes
Added ei.cfg to sources\ directory. You *HAVE* to extract the iso and
delete the file if you want to upgrade from a previous version of
Windows. Use the win81-pkeys.txt on the ISO for install keys
Office Professional Plus 2013 enables you to work together even better by
giving you more control over compliance, new tools for analyzing and sharing
data, and more possibilities for communication. Plus, Access, Lync and InfoPath
are included in the suite
Downlaod Windows 8.1 Preactived V2 Office 2013 Pro Plus (AlbDll.com) 4 G

Password for Zip Archive is : AlbDll.com
Windows 7 Sp1 Ultimate en-US (x64)
If you want to run Windows 7 on your PC, here's what it takes:
- 1 gigahertz (GHz) or faster 32-bit (x86) or 64-bit (x64) processor
- 1 gigabyte (GB) RAM (32-bit) or 2 GB RAM (64-bit)
- 16 GB available hard disk space (32-bit) or 20 GB (64-bit)
- DirectX 9 graphics device with WDDM 1.0 or higher driver
Additional requirements to use certain features:
- Internet access (fees may apply)
- Depending on resolution, video playback may require additional memory and advanced graphics hardware
- Some games and programs might require a graphics card compatible with DirectX 10 or higher for optimal performance
- For some Windows Media Center functionality a TV tuner and additional hardware may be required
- Windows Touch and Tablet PCs require specific hardware
- HomeGroup requires a network and PCs running Windows 7
- DVD/CD authoring requires a compatible optical drive
- BitLocker requires Trusted Platform Module (TPM) 1.2
- BitLocker To Go requires a USB flash drive
- Windows XP Mode requires an additional 1 GB of RAM and an additional 15 GB of available hard disk space.
- Music and sound require audio output
PCs with multi-core processors:
Windows 7 was designed to work with today's multi-core processors. All 32-bit versions of Windows 7 can support up to 32 processor cores, while 64‑bit versions can support up to 256 processor cores.
PCs with multiple processors (CPUs):
Commercial servers, workstations, and other high-end PCs may have more than one physical processor. Windows 7 Professional, Enterprise, and Ultimate allow for two physical processors, providing the best performance on these computers. Windows 7 Starter, Home Basic, and Home Premium will recognize only one physical processor.
Downlaod Windows 7 Sp1 Ultimate en-US (x64) (AlbDll.com) 4 G
Password for Zip Archive is : AlbDll.com
Friday, February 20, 2015
Maximum Security - A Hacker's Guide to Protecting Your Internet and Network (e-book)
Now more than ever, it is imperative that users be able to protect their system from hackers trashing their Web sites or stealing information. Written by a reformed hacker, this comprehensive resource identifies security holes in common computer and network systems, allowing system administrators to discover faults inherent within their network- and work toward a solution to those problems.
Downlaod Maximum Security - A Hacker's Guide to Protecting Your Internet and Network (e-book)
Machine Learning For Hackers (e-book)
If you’re an experienced programmer interested in crunching data, this book will get you started with machine learning—a toolkit of algorithms that enables computers to train themselves to automate useful tasks. Authors Drew Conway and John Myles White help you understand machine learning and statistics tools through a series of hands-on case studies, instead of a traditional math-heavy presentation.
Each chapter focuses on a specific problem in machine learning, such as classification, prediction, optimization, and recommendation. Using the R programming language, you’ll learn how to analyze sample datasets and write simple machine learning algorithms. Machine Learning for Hackers is ideal for programmers from any background, including business, government, and academic research.
- Develop a naïve Bayesian classifier to determine if an email is spam, based only on its text
- Use linear regression to predict the number of page views for the top 1,000 websites
- Learn optimization techniques by attempting to break a simple letter cipher
- Compare and contrast U.S. Senators statistically, based on their voting records
- Build a “whom to follow” recommendation system from Twitter data
Download Kingpin - Machine Learning For Hackers (e-book)

Thursday, February 19, 2015
Back | Track 5 R3
The time has come to refresh our security tool arsenal – BackTrack 5 R3 has been released. R3 focuses on bug-fixes as well as the addition of over 60 new tools – several of which were released in BlackHat and Defcon 2012. A whole new tool category was populated – “Physical Exploitation”, which now includes tools such as the Arduino IDE and libraries, as well as the Kautilya Teensy payload collection.
Building, testing and releasing a new BackTrack revision is never an easy task.Keeping up-to-date with all the latest tools, while balancing their requirements of dependencies, is akin to a magic show juggling act. Thankfully, active members of our redmine community such as backtracklover and JudasIscariot make our task that much easier by actively reporting bugs and suggesting new tools on a regular basis. Hats off to the both of you.
We would like to thank Offensive Security for providing the BackTrack dev team with the funding and resources to make all of this happen. Also, a very special thanks to
Downlaod Back | Track 5 R3 32Bit(AlbDll.com).7z 3 Gb
Password for 7zip Archive is : AlbDll.com
Back Track 4 R2
“BackTrack is a Linux-based penetration testing arsenal that aids security professionals in the ability to perform assessments in a purely native environment dedicated to hacking. Regardless if you’re making BackTrack your primary operating system, booting from a LiveDVD, or using your favorite thumbdrive, BackTrack has been customized down to every package, kernel configuration, script and patch solely for the purpose of the penetration tester.“
This is the official change log for the update:
- Kernel 2.6.35.8 – *Much* improved mac80211 stack.
- USB 3.0 support.
- New wireless cards supported.
- All wireless Injection patches applied, maximum support for wireless attacks.
- Even *faster* desktop environment.
- Revamped Fluxbox environment for the KDE challenged.
- Metasploit rebuilt from scratch, MySQL db_drivers working out of the box.
- Updated old packages, added new ones, and removed obsolete ones.
- New BackTrack Wiki with better documentation and support.
- Our most professional, tested and streamlined release ever.This release comes with faster Desktop responsiveness, better hardware support, broader wireless cardsupport, streamlined work environment. It also has the new kernel.
- Even *faster* desktop environment.
- Revamped Fluxbox environment for the KDE challenged.
- Metasploit rebuilt from scratch, MySQL db_drivers working out of the box.
- Updated old packages, added new ones, and removed obsolete ones.
- New BackTrack Wiki with better documentation and support.
- Our most professional, tested and streamlined release ever.This release comes with faster Desktop responsiveness, better hardware support, broader wireless cardsupport, streamlined work environment. It also has the new kernel.
This release comes with faster Desktop responsiveness, better hardware support, broader wireless cardsupport, streamlined work environment. It also has the new kernel.
Downlaod Back Track 4 R2 (AlbDll.com).7z 2 G
Password for Zip Archive is : AlbDll.com
Kingpin - How One Hacker Took Over (e-book)
Former hacker Kevin Poulsen has, over the past decade, built a reputation as one of the top investigative reporters on the cybercrime beat. In Kingpin, he pours his unmatched access and expertise into book form for the first time, delivering a gripping cat-and-mouse narrative—and an unprecedented view into the twenty-first century’s signature form of organized crime.
The word spread through the hacking underground like some unstoppable new virus: Someone—some brilliant, audacious crook—had just staged a hostile takeover of an online criminal network that siphoned billions of dollars from the US economy.
The FBI rushed to launch an ambitious undercover operation aimed at tracking down this new kingpin; other agencies around the world deployed dozens of moles and double agents. Together, the cybercops lured numerous unsuspecting hackers into their clutches. . . . Yet at every turn, their main quarry displayed an uncanny ability to sniff out their snitches and see through their plots.
The culprit they sought was the most unlikely of criminals: a brilliant programmer with a hippie ethic and a supervillain’s double identity. As prominent “white-hat” hacker Max “Vision” Butler, he was a celebrity throughout the programming world, even serving as a consultant to the FBI. But as the black-hat “Iceman,” he found in the world of data theft an irresistible opportunity to test his outsized abilities. He infiltrated thousands of computers around the country, sucking down millions of credit card numbers at will. He effortlessly hacked his fellow hackers, stealing their ill-gotten gains from under their noses. Together with a smooth-talking con artist, he ran a massive real-world crime ring.
And for years, he did it all with seeming impunity, even as countless rivals ran afoul of police.
Yet as he watched the fraudsters around him squabble, their ranks riddled with infiltrators, their methods inefficient, he began to see in their dysfunction the ultimate challenge: He would stage his coup and fix what was broken, run things as they should be run—even if it meant painting a bull’s-eye on his forehead.
Through the story of this criminal’s remarkable rise, and of law enforcement’s quest to track him down, Kingpin lays bare the workings of a silent crime wave still affecting millions of Americans. In these pages, we are ushered into vast online-fraud supermarkets stocked with credit card numbers, counterfeit checks, hacked bank accounts, dead drops, and fake passports. We learn the workings of the numerous hacks—browser exploits, phishing attacks, Trojan horses, and much more—these fraudsters use to ply their trade, and trace the complex routes by which they turn stolen data into millions of dollars. And thanks to Poulsen’s remarkable access to both cops and criminals, we step inside the quiet, desperate arms race that law enforcement continues to fight with these scammers today.
Ultimately, Kingpin is a journey into an underworld of startling scope and power, one in which ordinary American teenagers work hand in hand with murderous Russian mobsters and where a simple Wi-Fi connection can unleash a torrent of gold worth millions.
Download Kingpin - How One Hacker Took Over (e-book)
iOS Hacker's Handbook Honest (e-book)
Discover all the security risks and exploits that can threaten iOS-based mobile devices
iOS is Apple's mobile operating system for the iPhone and iPad. With the introduction of iOS5, many security issues have come to light. This book explains and discusses them all. The award-winning author team, experts in Mac and iOS security, examines the vulnerabilities and the internals of iOS to show how attacks can be mitigated. The book explains how the operating system works, its overall security architecture, and the security risks associated with it, as well as exploits, rootkits, and other payloads developed for it.
Covers iOS security architecture, vulnerability hunting, exploit writing, and how iOS jailbreaks work
Explores iOS enterprise and encryption, code signing and memory protection, sandboxing, iPhone fuzzing, exploitation, ROP payloads, and baseband attacks
Also examines kernel debugging and exploitation
Companion website includes source code and tools to facilitate your efforts
iOS Hacker's Handbook arms you with the tools needed to identify, understand, and foil iOS attacks.
Downlaod iOS Hacker's Handbook Honest (e-book) .pdf
Hacking The Xbox 360 For Dummies (e-book)
This is the best guide i have found for hacking the 360. It tells you everything from hacking your firmware to backing up games.
Description
Finally updated the firmware tutorial with all the new stuff! Only included the .pdf this time, but navigation is very much improved. There is now bookmarks to the left that will make finding your place much easier - use the bookmarks!
Enjoy!
Downlaod Hacking The Xbox 360 For Dummies (e-book) .pdf
Nik Software - Silver Efex Pro 2 Review
Create Stunning Black and White Digital Photos
(You can now get 75% off of the original price of the ENTIRE NIK Collection from Google when you use Coupon code KENK)
While there are countless ways to create black and white digital photographs today, Nik software’sSilver Efex Pro 2 stands out as my preferred method of creating Rich and beautiful black and white images in the digital darkroom.
I spent many years in real darkrooms back at the beginning of my career in photography. I think that having that background allows me to have a deeper appreciation of what is possible to do with digital images today on a computer. We are living in a golden age of photography where the possibilities for creating incredible images is near limitless.
While programs like Lightroom, Aperture, and Photoshop are quite capable of creating excellent black-and-white images, Silver Efex Pro 2 offers incredible diversity along with simplicity for the user. Anyone who is serious about black and white photography needs to try this excellent plug-in.
Luckily, there is a 15 day free trial of the software that allows you to test the full version with no limitations.
Intuitive Flexibility and Versatility
This software can be as intricate or as simple as you would like it to be, making it a solid choice for both amateur and professional photographers.
Some of my favourite features of the software are the possibility to emulate types of film, adding filters, total control of “film” grain, controlling image structure, one-click toning, and Nik’s U Point® Technology. While I’m using Silver Efex Pro 2 as a Photoshop plug-in, you can also use it as a stand alone product or in Lightroom and Aperture.
Let’s take a closer look.
The Silver Efex 2 workspace
The workspace is divided into 3 basic parts:
1- The Presets
1- The Image Preview
1- The Adjustment Panel or Tools
While you get a somewhat passable result in the neutral, there is no one button solution to creating a striking black and white image. The quick and easy way is to test some of the presets. If you want a quick conversion then one of the dozens of presets may very well be all you need to use. If however, you are more like me, then starting with one of the presets is a good place to begin before fine tuning the image with the robust adjustment tools at your disposal.
Each preset contains adjustments in brightness, contrast, structure, tone, film grain, and more. The serious photographer can use some of these presets as a starting point but will want to edit and fine tune the image more specifically to his or her needs.
Silver Efex Pro 2 presets with a split before & after preview screen
Less is more
As with so many other image editing plug-ins (as well as in Photoshop itself) going to the extreme possibilities can lead to destructive results to your image. Knowing when to stop is one of the keys of producing high-quality digital photographs. The controls in Silver Efex Pro 2 are extremely in-depth yet simple enough to use.
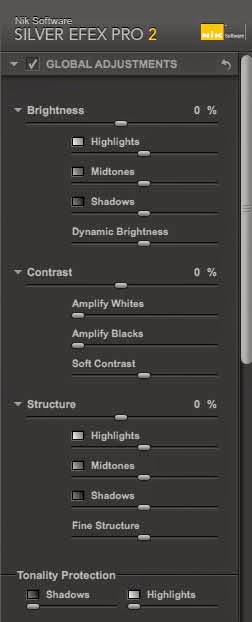
Global Adjustments
Global Adjustments
In this panel you control the typical brightness and contrast within the image. Two excellent features within this panel our dynamic brightness and soft contrast.
With the dynamic brightness slider Silver Efex Pro 2 does some of the thinking for you. The unique algorithms within the software assesses the different areas of your image and takes that information into consideration to give you a much smoother blending of overall brightness.
The soft contrast slider also will intelligently assess the overall contrast of your image and allow you to make subtle yet striking changes to the photograph you are working on. You really have to play with this slider in order to fully appreciate what you can do for you. It is a great addition to the plug-in.
Structure is one of my favorite parts of this software. Partly a sharpening tool, partly a depth tool; structure adds that extra bit of “oomph” to a photograph that takes it to the next level in terms of image detail.
Control Points
I love this feature. Control points allow you to selectively manipulate global adjustments in specific areas of your image. You can add as many control points as you wish to the image you are editing and control the size of each one individually. The top slider is the size slider which controls the area that you wish to adjust. The adjustment area is represented by the circle you see in the photo above. Dragging the slider left and right allows you to increase and decrease the size of each control. Below that slider are the enhancement sliders that give you full control over global adjustments in each individual control point.
With pinpoint precision you can adjust everything from brightness, contrast, structure, and even add color back to specific parts of your image. The selective adjustment control point tool is a very powerful feature yet amazingly easy to use.
Filter Efects
Filters
Back when we were all still using film cameras, it was customary to use coloured filters on our lenses in order to achieve certain books to our black-and-white images. The same effects can now be achieved in Silver Efex Pro 2 with the colour filter palette. In fact you have far more control now than ever before since you can manipulate these filters from 0 to 200% intensity as well as select any color in the spectrum by using the hue slider to choose any colour you could possibly want.
Once again starting with the presets is a good starting point but certainly not a one-button solution. Carefully selecting hue and strength allows you to have incredible control over the colour filter tool. In the thumbnails above you will see how each filter reacts to a vividly colourful photograph at 100% intensity. Using the colour filters in conjunction with global adjustments, selective control points, film grain, and toning allow you to make stunning black-and-white or monochromatic images.
Grain Engine
Like so many of the other features in Silver Efex Pro 2, the grain engine is extremely versatile and delivers near unlimited possibilities in terms of grain structure within your black and white images. When are used to shoot with film I was a big fan of high grain films from Kodak, Fuji, and Ilford. Today I gravitate much more towards high definition low grain images. There still is a place for grain in photography though, especially in black and white photographs. With precision control of the grain engine it has never been easier to create beautiful high grain black and white digital photos.
Toning menu with drop-down presets
Toning
I’ve always been a big fan of sepia and selenium toning of black and white photographs but I sure never enjoyed the horrible chemical smells especially when working with sepia toners in a traditional darkroom. This is just one more reason why I love working on digital imaging which gives me far more versatility and is far better for the environment as well. Like the other tools in Silver Efex pro 2 the toning tools are quite extensive.
You can use any of the 24 different presets for toning your images or create your own unique tones and save those as presets as well.
Toning
I’ve always been a big fan of sepia and selenium toning of black and white photographs but I sure never enjoyed the horrible chemical smells especially when working with sepia toners in a traditional darkroom. This is just one more reason why I love working on digital imaging which gives me far more versatility and is far better for the environment as well. Like the other tools in Silver Efex pro 2 the toning tools are quite extensive.
You can use any of the 24 different presets for toning your images or create your own unique tones and save those as presets as well.
Vignettes and Burnt Edges
Creating custom vignettes has never been easier. Using the vignette and burnt edges tool allows you to darken or lighten the edges of your photo with good accuracy. Once again you can start with one of several presets and fine tune the results quite nicely with the different adjustment sliders.
Image Borders
This is one of the only parts of the software that I find lacking. Image borders are tricky and also very subjective in terms how people judge them. Is a border really necessary? I’d say that in 100% of commercial professional photography applications the answer would be no. They just risk looking tacky. While I do like the use of image borders in iPhone or Android photography, those are just fun and playful ways of sharing snapshots. If your professional images require a fancy border to make them good, then it’s not saying much about the images.
These borders are customizable to a degree . There are several standard presets that you can fine tune but you can’t save your favourites as custom presets. Even if I doubt that I’ll use this feature much, the borders are relatively well done and certainly fitting in style for use along with black and white photography. There is room for improvement here though.
Presets
Silver Efex Pro 2 allows you to use any of its already existing presets but you can also create your own. Once you achieve an overall look that you enjoy, clicking the “Add Preset” button at the bottom left of your screen will allow you to save and name your own custom presets. Now with one click you can re-create your favourite overall looks on any new image that you are working on.
Creating and naming your own custom presets by using the selective tools can be a great time saver for future projects.
Pros and Cons
If when you are reading this review you feel like I’m not finding anything wrong with the Silver Efex Pro 2, you’re close to being correct. While I don’t do a lot of black and white work anymore, when I do, this is my go to software.
On the plus side
- Amazing Versatility
- Speed
- Ease-of-use and navigation
- Pinpoint accuracy in adjusting select parts of your photograph with Nik’s “U point technology”
- Excellent overall image presets and toning presets
- Infinite possible end results
- The intuitive history browser similar to Photoshop’s history pallet
- Nik’s intelligent dynamic brightness, fine structure, and soft contrast sliders
- Compatibility with Photoshop, Lightroom, and Aperture
- Film Emulation with grain control
The down side
- Speed
- Ease-of-use and navigation
- Pinpoint accuracy in adjusting select parts of your photograph with Nik’s “U point technology”
- Excellent overall image presets and toning presets
- Infinite possible end results
- The intuitive history browser similar to Photoshop’s history pallet
- Nik’s intelligent dynamic brightness, fine structure, and soft contrast sliders
- Compatibility with Photoshop, Lightroom, and Aperture
- Film Emulation with grain control
The down side
Image Borders don’t support transparency on PNG files
It isn’t possible to see the original colour file while Silver Efex Pro 2 is active*
*Editor’s note: You can see the original colour image as was pointed out to me by the Nik team. I find the solution to be complicated and would love to see a simple “See Original Image” button that would allow you to revert to the colour image you began with as a preview at any point during your editing.
Here is the solution as given to me from Nik Software:
How to see the original colour file
a. Go to the History browser.
b. Click Compare once, this will have the History State Selector show up (this may seem like an odd UI, but when we always displayed the history state selector in the single image view mode, everyone that tested the software got really confused since the control didn’t do anything. It’s always visible in the side-by-side and split-view modes).
c. Drag the History State Selector to Original Image
d. Press and hold the Compare button
Wrap up
Nik Software offers some excellent tools for digital photographers and Silver Efex Pro 2 to me is their flagship plug-in. Not only does it work well and offer high end results that top photographers around the world are using but it is a lot of fun to work with. I do not say that about most software I use for work.
I’ve been wanting to share my Nik Silver Efex Pro 2 review for a while now but I kew it would take some time to cover all the features properly. This is a powerful and robust piece of software aimed at professional photographers and proficient amateurs. If you’re looking to take your black and white photography to the next level, then this software is exactly what you are looking for. Try the full product with no limitations for 15 days to see if it’s right for you.
Explore, Learn, Grow
Nik Software also offers several ways to learn how to use their products more efficiently. They offer webinars hosted by top professional photographers, on demand video tutorials, and a blog full of valuable hints and tips. All of this material is available for free.
Nik Software - Silver Efex Pro 2 (AlbDll.com) 33 Mb

Password for zip archive is : AlbDll.com
Subscribe to:
Posts (Atom)